 Wildcard SSL + PeopleSoft
Wildcard SSL + PeopleSoft
Out of the box you can do just about anything with WebLogic, however, when you get into some of the specifics and try to tie it into an application like PeopleSoft you can run into some interesting quirks. I personally really like wildcard SSL certificates because it cuts down on a huge administrative headache that can come from trying to manage certificates for every “name” that needs to be managed. In PeopleSoft you can have dozens of servers and it can get to be an administrative nightmare.
WebLogic allows you to store and reference the wildcard certificate in you keystore, however, Wildcard Host Name Verification will fail with default settings. If you do a quick google search you will turn up several posts that explain to simply “ignore” wildcard host name verification. I am not a fan of just “ignoring” things. So you could simply add the following to the start command of Weblogic:
-Dweblogic.security.SSL.ignoreHostnameVerification=true
However, I found what I consider a better option which is to set the validation to a custom wildcard host name verification with a delivered public class for WebLogic Security: SSLWLSHostnameVerifier, which can be called for hostname verification and will apply wildcard host name verification checks. This wildcard host name verification is instantiated by the WebLogic hostname verifier wrapper that checks for proxies, expectedName, etc. It obtains this hostname verifier class name from the SSLMBean or the hostname verifier property.
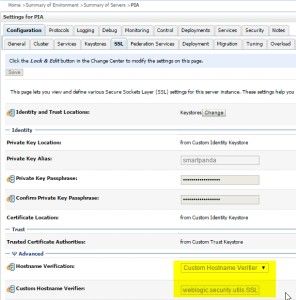 In the WebLogic Console:
In the WebLogic Console:
you can change the advanced SSL properties:
Hostname Verification:
Custom HostName Verification
Custom Hostname Verifier:
weblogic.security.utils.SSLWLSWildcardHostnameVerifier
This will do a check of the peer certificate of the SSL session’s peer certificate SubjectDN CommonName attribute supports wildcarding, the CommonName attribute must meet the following:
- the CN must have at least two dot (‘.’) characters
- the CN must start with “*.”
- the CN can have only one “*” character